Let’s Encrypt is a free, automated, and open certificate authority (CA), run for the public’s benefit. It is a service provided by the Internet Security Research Group (ISRG).
Let’s Encrypt gives people the digital certificates they need in order to enable HTTPS (SSL/TLS) for websites, for free, in the most user-friendly way we can. We do this because we want to create a more secure and privacy-respecting Web.
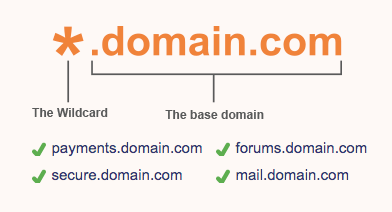
Wild Card: Wildcard SSL certificates allow you to secure the main domain and an unlimited number of sub-domains under the main domain. For example, test.abdelrhmangamal.com , example.abdelrhmangamal.com etc.
Wildcard SSL certificates offer full encryption for the subdomains, making them an affordable and effective solution for most websites.
This brief tutorial shows how to generate free wildcard SSL/TLS certificates using Let’s Encrypt (Certbot) on Ubuntu 16.04 | 18.04 LTS
Step 1: Install Let’s Encrypt Certbot
sudo apt update
sudo apt install letsencryptOther installation method Here
Step 2: Generate Let’s Encrypt Wildcard SSL Certificate.
Before going with this step make sure you already have your domain with the proper IP address pointed to it. then execute the below command.
However, for wildcard certificates, the only challenge method Let’s Encrypt accepts is the DNS challenge, which we can invoke via the preferred-challenges=dns flag.
sudo certbot certonly --manual --preferred-challenges=dns --email admin@example.com --server https://acme-v02.api.letsencrypt.org/directory --agree-tos -d example.com -d *.example.comThe command options above are explained below:
- –certonly: Obtain or renew a certificate, but do not install
- –manual: Obtain certificates interactively
- –preferred-challenges=dns: Use dns to authenticate domain ownership
- –server: Specify the endpoint to use to generate
- –agree-tos: Agree to the ACME server’s subscriber terms
- -d: Domain name to provide certificates for
Go to your DNS provider and add a text record for the string above and save.

